How I landed my first Internship offer
For those unfamiliar with Indian college placements(Recruitments): companies visit universities and run students through online tests, coding rounds, technical interviews, and HR discussions. If you survive the entire process, you graduate with a job offer before you even finish your degree.
Walmart Global Tech — The Unexpected Cybersecurity Journeyh2
When placement season started, I wasn’t expecting to interview for a Cybersecurity role. My work had mostly been in distributed systems, cloud, and backend stuff. I had a solid grounding in networks and knew my way around common OWASP vulnerabilities, but I had exactly zero “pure cybersec” projects.
Still, I decided to give it a shot.
Round 1: Warm and Simpleh2
The interviewer took one look at my resume and asked the most valid question possible:
“Are you sure you know this role is for cybersecurity?”
Fair question, considering my resume was full of cloud architecture and heavy systems stuff. I was honest with him. I explained that when you work with large-scale systems, security is pretty much built-in. I also pointed out that I’ve picked up complex subjects like Big Data in short periods before, so three months was enough for me to build a security foundation.
He appreciated the honesty, and we moved on to the technicals.
We didn’t just recite definitions. We walked through the OSI model by tracing what happens when you type google.com in a browser. We covered HTTPS, DNS, ports 443 and 53, and the TCP handshake. Then we shifted to attacks—ransomware basics, SQL Injection (I used a blind SQLi example), Nmap scanning, and how SSO and SAML actually work.
He was from the Blue Team (SecOps), so we also chatted about the difference between Red and Blue teaming. It felt less like an interrogation and more like a technical check-in.
Round 2: The Whiteboard Sessionh2
This was the fun part. He asked me to pick a project, so I chose my serverless lambda architecture. I walked up to the board and drew the entire flow. Compute, storage, metadata, logs, the whole thing.
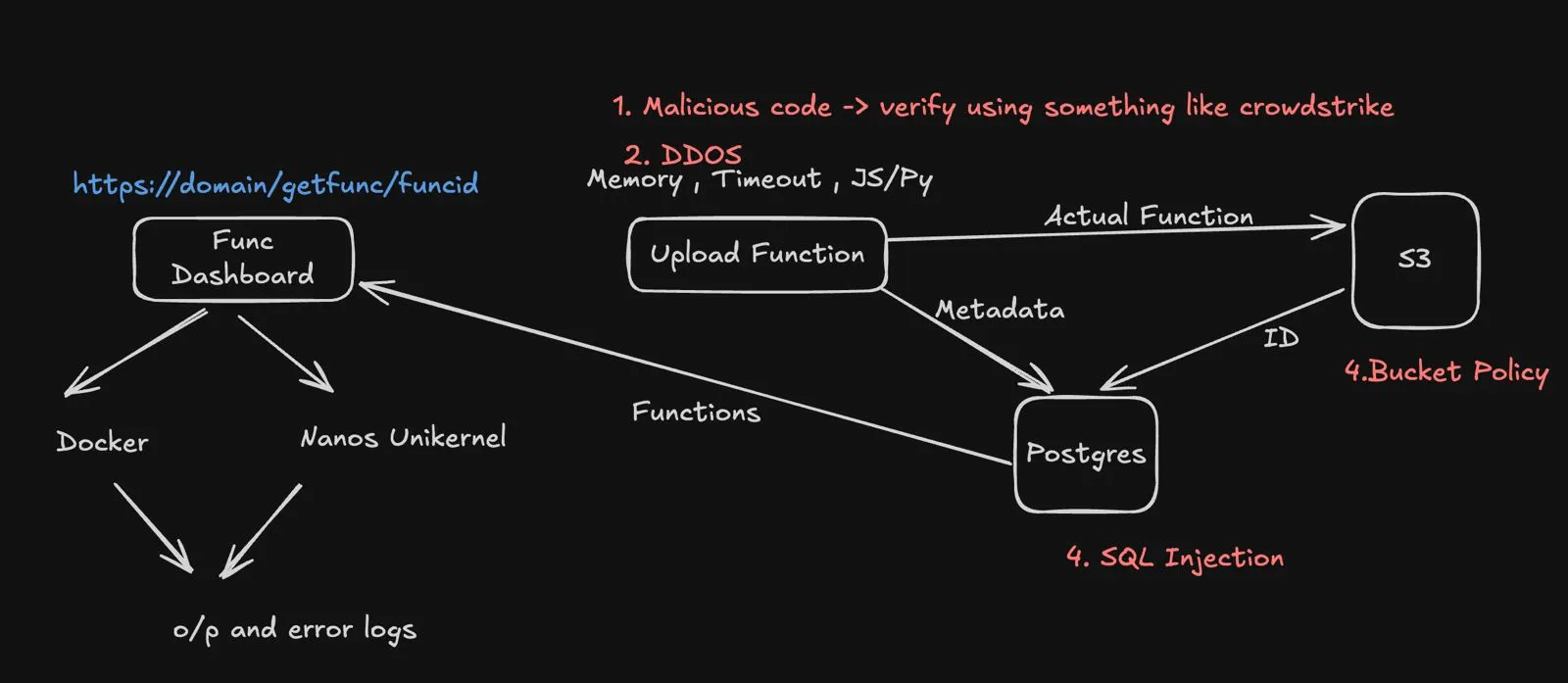 Rough sketch of what I drew on the whiteboard
Rough sketch of what I drew on the whiteboard
Then came the real test. He pointed at the board and said, “Identify potential cybersecurity vulnerabilities in that architecture and tell me how you’d fix them.”
We spent the rest of the interview trying to break my own design.
We talked about DDoS protection, and I wrote some rough pseudocode for a Leaky Bucket algorithm to handle rate limiting. When we discussed malicious code uploads, I suggested ML-based detection, and he recommended checking out tools like CrowdStrike.
We went deep into S3 bucket policies—least-privilege IAM, restricting public access, and the usual misconfigurations people make. We also debated where to place firewalls versus proxies versus IDS/IPS systems.
The discussion eventually drifted to web security. We covered CSRF, XSS, OAuth, and CORS. I actually learned something on the spot too—he asked about X-Frame-Options and explained how it prevents clickjacking.
He wrapped up by asking about code obfuscation, and the round ended pretty clean.
Round 3: The Hiring Managerh2
The Hiring Manager had that calm, experienced vibe. He’d worked with companies like Qualcomm and clearly knew his stuff.
This wasn’t a rapid-fire technical round. It was a bigger picture conversation. We talked about how firewalls have evolved and how modern IDS/IPS systems differ from the early filtering days. We even got into the security concerns around LLMs.
He explained how Walmart’s cybersec teams are structured and that they place candidates based on strengths. I told him I enjoy both development and security work, and he was completely fine with that.
The Offerh2
I got the offer the very same day, late in the evening on October 13, 2025.
It was surreal. I went into that interview room unsure if I even belonged there because of my background, and I came out with an offer from one of the biggest tech companies in the world.
Looking Backh2
Reflecting on the whole process, I think honesty is what saved me. I didn’t pretend to be a cybersecurity wizard. I was upfront about my background, and I used my strength in systems and networking to bridge the gap.
I also realized that curiosity beats credentials. I didn’t have the certifications, but being able to think on my feet and draw architecture on a whiteboard mattered more than having the right keywords on my resume.
Your journey doesn’t have to look like everyone else’s. It just has to be yours.
Comments